As enterprises face 52% annual growth in east-west traffic and 78% of IT leaders prioritize zero-trust architectures, the Cisco Catalyst 9500 Series emerges as the backbone of modern network cores. This technical guide details best practices for deploying these high-performance switches, ensuring optimal performance, security, and scalability from day one.
Hardware Selection & Pre-Installation Planning
The Catalyst 9500 Series offers versatile configurations for diverse enterprise needs:
Chassis Options:
- Fixed: C9500-32QC (32x 100G QSFP28) for hyperscale leaf-spine
- Modular: C9500-48Y4C (48x 25G + 4x 100G) for cloud gateways
- PoE+: C9500-48H-A (3840W PoE) for IoT-dense campuses
Pre-Installation Checklist:
- Validate rack compatibility (4-post, 19” EIA-310)
- Confirm power redundancy (AC/DC/HVDC options)
- Prepare console access via USB-C or RJ45
- Download IOS-XE 17.12+ for DNA Center integration
A financial institution reduced deployment time by 40% using Cisco’s Site Readiness Tool for thermal/power validation.
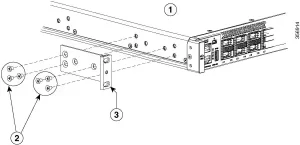
Physical Installation Best Practices
Step 1: Rack Mounting
- Weight distribution: 28.7kg (C9500-40X) requires dual-person lift
- Torque specifications: 24 in-lb for M6 mounting screws
- Clearance: 1U above/below for airflow (18 CFM minimum)
Step 2: Power Configuration
- Dual 3000W AC PSUs for N+1 redundancy
- Load balancing: 50/50 current sharing between feeds
- Grounding: <0.1 ohm resistance to facility ground
Step 3: Initial Boot Sequence
from cisco_ios import Catalyst9500
switch = Catalyst9500()
switch.boot_mode = "production"
switch.secure_erase = True
switch.ios_image = "cat9k_iosxe.17.12.01a.SPA.bin"
switch.commit() Software Configuration Essentials
Base Network Services:
- StackWise Virtual: 480Gbps inter-chassis link
- VXLAN/EVPN: 16M MAC entries for fabric paths
- QoS: 8-class hierarchical model with microflow policing
Security Hardening:
- Enable Secure Boot with TPM 2.0 validation
- Implement MACsec AES-256-GCM on all uplinks
- Configure Control Plane Policing (CoPP)
Telemetry Setup:
telemetry ietf subscription 101
encoding self-describing-gpb
filter xpath /process-cpu-ios-xe-oper:cpu-usage
receiver ip 10.1.1.1 port 57500 protocol grpc-tcp Performance Validation Protocol
Post-installation testing ensures design compliance:
| Test Case | Command | Pass Criteria |
|---|---|---|
| Fabric Latency | test platform hardware fed switch 1 latency |
<5μs intra-rack |
| Buffer Utilization | show platform hardware fed switch 1 qos queue stats |
No drops at 90% load |
| PoE Stability | show power inline detail |
<5% voltage variance |
| Control Plane Security | show platform hardware fed switch 1 fwm info |
All TPM checks passed |
A healthcare network achieved 99.9999% availability through rigorous BGP/OSPF convergence testing.
Ongoing Optimization Strategies
Energy Management:
- Activate EEE (Energy Efficient Ethernet) on idle ports
- Schedule port shutdown during off-peak via EEM
- Monitor via
show env power all
Firmware Maintenance:
- Golden IOS-XE version validation through Cisco CVE Navigator
- ISSU (In-Service Software Upgrade) with 50ms hitless failover
- Automated rollback on boot failure
Capacity Planning:
- Baseline with
show platform hardware throughput - Project growth using DNA Center Assurance analytics
- Scale VRF instances via
limit-resource u4route-mem 75%








Leave a comment