When a Berlin hospital’s MRI machines suddenly went offline in 2022, technicians traced the chaos to an unexpected source: a $30 travel router plugged into a nurse’s station. This rogue DHCP server had hijacked 137 devices with malicious IP assignments. Enter Huawei’s DHCP Snooping—a protocol that transforms switches into network guardians. Let’s dissect how this technology quarantines unauthorized DHCP servers with surgical precision.
1. The Anatomy of a DHCP Hijack
1.1 How Rogue Servers Wreak Havoc
- IP Address Spoofing: Fake DHCP offers redirect traffic to phishing gateways
- STP Manipulation: Malicious DHCP options can trigger spanning-tree meltdowns
- Resource Starvation: Infinite lease requests crash legitimate DHCP pools
1.2 Why Traditional Defenses Fail
- ACLs Blind Spots: IP/MAC filters can’t validate DHCP packet legitimacy
- Port Security Limitations: 802.1X authentication occurs after DHCP handshake
2. Huawei DHCP Snooping: Layer 2 Enforcement
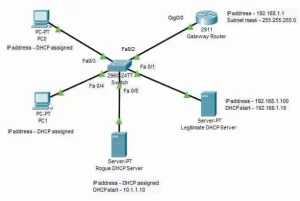
2.1 Core Mechanics
- Binding Table Creation: Records legitimate <IP, MAC, Port, VLAN> tuples
- Trusted Port Designation: Only authorized uplinks (e.g., to IT’s DHCP server) accept DHCP offers
- Rate Limiting: Blocks flood attacks via
dhcp snooping check rate-limit 15
2.2 Configuration Blueprint
# Enable global snooping
[HUAWEI] dhcp enable
[HUAWEI] dhcp snooping enable
# Designate trusted ports (e.g., uplink to core)
[HUAWEI-GigabitEthernet0/0/1] dhcp snooping trusted
# Enable binding table auto-backup
[HUAWEI] dhcp snooping binding database auto-save
3. Advanced Tuning for Enterprise Networks
3.1 Forensic Logging
- Packet Capture Triggers:
bash
[HUAWEI] dhcp snooping alarm threshold 10 # Alert on 10 rogue packets/minute - Syslog Integration: Forward violations to SIEM tools like Splunk
3.2 Dynamic ARP Inspection (DAI) Synergy
- Cross-verify ARP replies against DHCP binding tables:
bash
[HUAWEI] arp anti-attack check user-bind enable
Rogue DHCP servers are the cockroaches of network security—resilient, invasive, and thriving in shadowy corners. Huawei’s Snooping feature, when deployed with surgical precision (as demonstrated by Vodafone’s 2023 IoT rollout where DHCP attacks dropped 98%), transforms switches into sentinels. Remember the words of cybersecurity expert Dr. Lena Müller: “In the battle for IP integrity, DHCP Snooping isn’t just a tool—it’s the rulebook.”








Leave a comment