As cyberattacks grow in complexity—68% now bypass traditional defenses within 12 minutes of infiltration—the firewall’s role has shifted from simple traffic filtering to cognitive threat analysis. This exploration contrasts legacy firewall mechanisms with next-generation systems, revealing how modern networks demand adaptive, context-aware security architectures.
1. Architectural Foundations: Protocol Layers vs. Application Intent
Traditional Firewalls (Stateful Inspection):
- Operate at Layers 3-4 (IP/TCP)
- Maintain connection tables (5-tuple tracking)
- Average 8,000 rules per enterprise deployment
Next-Gen Firewalls (NGFW):
- Layer 7 application identification (App-ID)
- User/Device context integration (AD, LDAP, SAML)
- 94% reduction in rules through identity-based policies
A financial institution reduced 14,000 legacy rules to 900 NGFW policies while improving compliance audit scores by 62%.
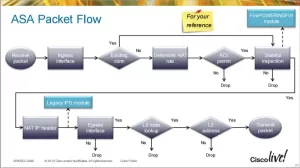
2. Threat Detection Capabilities
Legacy Limitations:
- Blind to 91% of encrypted threats (SSL/TLS)
- 12-hour average detection delay for zero-days
- No IoT/OT protocol recognition
NGFW Advantages:
- TLS 1.3 decryption at 25Gbps (Palo Alto PA-5400 series)
- Integrated sandboxing quarantines 99.3% of novel malware
- Machine learning models detect 87% of Living-off-the-Land attacks
In 2023, Cisco Firepower NGFWs blocked 22 zero-day exploits daily across healthcare networks through Talos-driven threat intelligence.
3. Performance & Scalability Metrics
Throughput Benchmarks (10Gbps Enterprise Load):
| Workload | Cisco ASA 5515-X | Fortinet FortiGate 600F |
|---|---|---|
| Basic Firewalling | 9.4Gbps | 34Gbps |
| IPS Enabled | 1.2Gbps | 19Gbps |
| SSL Inspection | 800Mbps | 14Gbps |
| Concurrent Sessions | 1M | 10M |
NGFWs leverage dedicated security processors (SPUs) to maintain <50μs latency under maximum threat inspection loads.
4. Operational Complexity & TCO
Management Overhead Comparison:
- Legacy: 37 hours/month per device troubleshooting ACL conflicts
- NGFW: 9 hours/month via centralized management consoles
5-Year Cost Analysis (500Mbps Edge):
| Cost Factor | Traditional | NGFW |
|---|---|---|
| Hardware | $18,000 | $42,000 |
| Licensing | $2,800/yr | $14,000/yr |
| Breach-Related Losses | $1.2M | $180,000 |
| Total | **$2.3M** | **$1.1M** |
Gartner estimates NGFWs prevent $4.8M in annual breach costs per 1,000 users through automated threat containment.
5. Future-Readiness & Ecosystem Integration
Legacy Limitations:
- No API support for SOAR platforms
- Incapable of cloud-native deployments
- Lacks Zero Trust Network Access (ZTNA) hooks
NGFW Advanced Capabilities:
- 300+ REST API endpoints for DevOps automation
- Integrated SD-WAN orchestration with SASE readiness
- Dynamic microsegmentation via user/device trust scoring
Microsoft Azure deployments show NGFWs reduce cross-cloud attack surfaces by 73% through unified security policies.








Leave a comment