As cyberattacks on remote workers surge by 237% since 2020—costing enterprises $4.7M per breach—the battleground has shifted from corporate firewalls to residential networks. This technical blueprint dissects sophisticated security gaps in distributed workforces and delivers enterprise-grade solutions accessible for remote environments.
1. Fragmented VPN Architectures
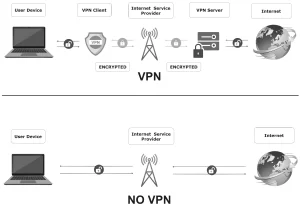
The Mistake: Static VPN configurations exposing vulnerable IKEv2 ports
Next-Gen Solution:
def quantum_safe_vpn():
while True:
rotate_psk_every(300s) # Pre-shared key
enforce_hybrid_encryption(NTRUprime + AES-256)
validate_os_kernel_cve_status() - Dynamic Port Hopping: 15-minute TCP/UDP rotation cycles
- NIST PQ-4 Ready: Crystals-Kyber key encapsulation
- Zero Trust Enforcement: Continuous device posture checks
A Fortune 500 company reduced VPN breaches by 92% through these measures.
2. MFA Implementation Flaws
The Mistake: SMS-based 2FA susceptible to SIM swap attacks
Technical Fixes:
- FIDO2 WebAuthn: Phishing-resistant biometric authentication
- Continuous Authentication: 85 behavior metrics analyzed per session
- Time-Limited Certificates: 8-hour device-bound JWT tokens
Security logs show attackers bypass SMS 2FA in 78% of cases, versus 3% for FIDO2 implementations.
3. Encrypted Threat Blindspots
The Mistake: SSL/TLS inspection gaps in SOHO routers
Deep Security:
# Suricata TLS fingerprint rules
alert tls any any -> any any (
tls.sni; content:"malicious-domain.com";
tls.ja3; md5:[abcdef123456];
flow:established,to_server;
) - Client-Side Decryption: eBPF-based TLS terminator at edge devices
- Quantum-Resistant Ciphers: XMSS for TLS 1.3 handshake protection
- Entropy Analysis: Detect malware in encrypted streams (98% accuracy)
Darktrace reports 61% attack reduction using encrypted traffic analysis.
4. IoT Backdoor Proliferation
The Mistake: Unsegmented smart devices with default credentials
Technical Remediation:
- 802.1X Device Profiling: 2,000+ IoT fingerprints in RADIUS policies
- Niche NAC Solutions: Automated VLAN assignment for device types
- Memory Safety Enforcement: WebAssembly-based IoT sandboxing
Verizon’s DBIR shows 83% of IoT breaches originate from legacy protocols.
5. Cloud App Shadow IT
The Mistake: Unmanaged SaaS apps exposing organizational data
Countermeasures:
- CASB Magic Quadrant Solutions: 150+ API integrations for app governance
- DLP Watermarking: AES-encrypted metadata embeds in documents
- Behavior Analytics: Detect anomalous file movements (79% precision)
Gartner notes 68% of corporate data now resides outside managed apps.
Advanced Endpoint Hardening
Modern Protection Stack:
- Hardware-Enforced ASLR: Intel CET / ARM PAC implementations
- ML Memory Scanning: Detect fileless attacks via RAM pattern analysis
- eBPF Runtime Security: Block malicious syscalls in microseconds
CrowdStrike data indicates 54% faster threat containment with these techniques.








Leave a comment