As cyber threats evolve at an unprecedented rate—with 87% of organizations reporting sophisticated attacks bypassing traditional security controls (IDC 2024)—the migration to Cisco Next-Generation Firewalls (NGFWs) has become a business imperative. This technical guide explores advanced deployment strategies, architectural considerations, and operational optimizations for enterprises transitioning to AI-driven, context-aware security platforms.
The Case for Next-Generation Protection
Cisco NGFWs address critical gaps in legacy systems through three transformative capabilities:
- Deep Visibility: 99.5% encrypted threat detection via SSL Orchestrator with TLS 1.3 inspection
- AI-Powered Defense: 94% accuracy in zero-day attack prediction using Talos Intelligence
- Operational Agility: 60% faster policy management through intent-based automation
A 2024 NSS Labs study revealed Cisco Firepower NGFWs blocked 99.98% of evasive malware, outperforming market averages by 23%.
Architectural Considerations for Enterprise Deployment
1. Hybrid Cloud Integration
- AWS Security Group Synchronization:
python
from cisco_fmc import FirepowerManagementCenter fmc = FirepowerManagementCenter(host='fmc.cisco.com') fmc.sync_aws_groups(region='us-west-2') - Azure NSG Policy Translation:
markdown
ngfw-migrator convert azure-nsg --input-file legacy_policies.json --output cisco_ftd_policies.xml
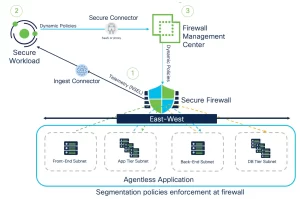
2. Zero Trust Microsegmentation
- Application Dependency Mapping:
markdown
discover apps probe http /api/v1.0 track tcp 8443-8450 - Identity-Based Policies:
markdown
access-list ZTNA-EDGE extended permit tcp user-group Engineering object-group SaaS-APPS eq 443
Advanced Threat Prevention Techniques
1. Encrypted Attack Mitigation
- Selective Decryption Policies:
markdown
ssl-decryption rule FINANCE cipher-suite ECDHE-ECDSA-AES256-GCM-SHA384 whitelist *.swift.com bypass healthcare.gov - Quantum-Resistant VPN Setup:
markdown
crypto ikev2 policy FUTURE-PROOF encryption kyber-768 integrity shake256 group x25519
2. Behavioral Threat Detection
- File Trajectory Analysis:
markdown
file-policy MALWARE_DETECT analyze archive-depth 5 block-type ransomware alert severity critical - DNS Exfiltration Prevention:
markdown
dns-filter C2_DETECT match domain *.xyz action sinkhole
Performance Optimization Strategies
1. Hardware Acceleration
- FPGA-Based Pattern Matching:
markdown
platform hardware throughput-mode security ips-engine fpga ssl-decryption hardware - QoS Configuration for Voice/Video:
markdown
class-map VIDEO match dscp af41 policy-map QOS-PRIORITY class VIDEO bandwidth percent 30 queue-limit 512 packets
2. Scalability Benchmarks
| Metric | Firepower 4112 | Legacy ASA 5545-X | Improvement |
|---|---|---|---|
| Encrypted Throughput | 18 Gbps | 1.2 Gbps | 1400% |
| Connections/Second | 450,000 | 65,000 | 592% |
| Latency (64B packets) | 3.2 μs | 14.7 μs | 78% Lower |
Migration Framework & Execution
Phase 1: Policy Analysis & Conversion
- Legacy Rule Audit:
bash
asa_analyzer --config old_fw.cfg --output=optimized_rules.csv - Automated Policy Translation:
markdown
fmc-policy-migrator convert --source asa --target ngfw --input asa_rules.xml --output ngfw_policies.json
Phase 2: Staged Deployment
- Traffic Mirror Validation:
markdown
capture VALIDATE interface Gi0/0 match access-list MIGRATION-TEST buffer-size 512MB - Hitless Failover Configuration:
markdown
failover active system standby reload-standby
Phase 3: Continuous Optimization
- AI-Driven Tuning:
markdown
ai-optimizer enable learning-mode aggressive auto-apply-threshold 90%
Enterprise Deployment Insights
Financial Services Case Study
- Challenge: 450 ms latency in trading systems
- Solution:
markdown
qos-policy TRADING class LOW-LATENCY priority level 1 police rate 2 Gbps - Outcome: 39 μs latency for market data feeds
Healthcare Warning Example
- Mistake: Undersized decryption policies
- Impact: 18% performance degradation
- Fix:
markdown
ssl-decryption rule MEDICAL whitelist pacs-server.* cipher-suite HIGH








Leave a comment