Selecting the right access layer switches represents one of the most critical decisions network administrators face when building or refreshing enterprise infrastructure. These devices form the fundamental connection point between end-user devices and the network backbone, directly impacting performance, security, and manageability for every connected user. With leading manufacturers including Cisco, Huawei, and Juniper offering diverse product lines like the Catalyst 2960X, S5700, and EX2300 series, the choice often comes down to specific organizational requirements rather than simply selecting a brand name. Understanding the technical considerations behind access switch selection enables enterprises to build networks that not only meet current needs but also adapt to evolving technological demands and business growth.
The access layer serves as the frontline of any network infrastructure, handling the constant traffic flow between user devices and network resources. These switches must balance performance requirements with cost considerations while providing the reliability that modern business operations demand. As enterprises increasingly rely on cloud applications, unified communications, and bandwidth-intensive services, the capabilities of access layer switches directly influence productivity and user experience. Making informed decisions at this level creates a foundation that supports rather than constraints organizational objectives, making the selection process far more significant than simply choosing between competing hardware vendors.
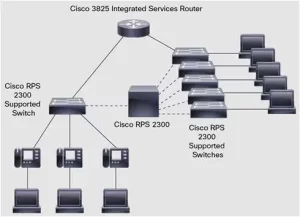
Understanding Network Layered Architecture
Modern enterprise networks typically employ a three-layer hierarchical design that divides functionality into distinct segments for optimized performance and management. This structured approach separates the network into core, distribution, and access layers, each serving specific purposes within the overall architecture. The core layer functions as the high-speed backbone, facilitating rapid data transfer between different network segments. Distribution layers provide policy-based connectivity between access and core layers, implementing security policies, quality of service, and routing between VLANs. The access layer represents the network edge where end devices initially connect, serving as the first point of contact for users and their equipment.
This hierarchical design offers numerous advantages over flat network architectures, including improved scalability, easier troubleshooting, and enhanced security through logical segmentation. By separating concerns across different layers, network administrators can implement targeted policies and upgrades without affecting the entire infrastructure. The access layer specifically handles the unique challenges of device connectivity, including authentication, basic traffic filtering, and initial quality of service implementation before passing traffic to the distribution layer for more sophisticated processing.
Access Layer Switch Fundamentals
Access layer switches typically feature high port densities with 10/100/1000Mbps copper connections, often supplemented with fiber uplink capabilities for connectivity to distribution layer devices. These switches operate as the network’s entry point, providing connectivity for wired devices including computers, printers, IP phones, and wireless access points. The term “Gigabit Ethernet switch” commonly refers to devices that offer Gigabit uplink capabilities while maintaining lower-speed access ports, though modern deployments increasingly standardize on Gigabit connectivity across all ports.
These devices typically support essential networking features including VLAN segmentation, basic quality of service policies, and port security features. The backplane bandwidth generally exceeds 8.8 Gbps in modern devices, ensuring non-blocking performance across all ports even during peak utilization periods. For small and medium businesses, access layer switches sometimes pull double duty as core network devices, though this approach becomes impractical as organizations scale beyond limited user counts or geographic locations.
Primary Functions and Responsibilities
Access layer switches perform several critical functions within the network ecosystem. They provide the physical connectivity for end-user devices, implementing the electrical and data link layer protocols that enable network communication. Beyond basic connectivity, these devices implement security policies at the network edge, including port security features that prevent unauthorized device connections and basic access control lists that filter inappropriate traffic.
These switches also handle initial quality of service implementation, marking traffic according to policies that ensure appropriate bandwidth allocation for latency-sensitive applications like voice and video. They aggregate user traffic before passing it to distribution layer switches, reducing the number of connections required at higher network layers. Additionally, managed access switches provide monitoring capabilities that help network administrators identify connectivity issues, bandwidth utilization patterns, and potential security concerns before they impact broader network performance.
Selection Criteria for Enterprise Environments
Choosing appropriate access layer switches requires careful consideration of both current requirements and future growth projections. Port density represents one of the most immediate concerns, with 24 and 48-port configurations representing the standard options for most deployment scenarios. Organizations should consider not only the number of currently required connections but also anticipated growth over the switch’s operational lifespan, typically three to five years in most enterprises.
Uplink capabilities deserve particular attention, as these connections carry aggregated traffic from all access ports to distribution layer devices. Modern deployments typically utilize 10Gbps uplinks, though specific requirements vary based on user count and application demands. Fiber optic uplinks generally provide better performance over longer distances, while copper connections offer cost savings in smaller deployments. Power over Ethernet capabilities have become increasingly important for supporting wireless access points, IP phones, and surveillance cameras without requiring separate power infrastructure.
Managed Versus Unmanaged Solutions
The decision between managed and unmanaged switches significantly impacts network security, monitoring capabilities, and troubleshooting options. Unmanaged switches provide basic connectivity without configuration interfaces, making them suitable for environments with minimal security requirements and no need for traffic segmentation or quality of service policies. These devices typically work well in small offices with limited technical staff and straightforward connectivity needs.
Managed switches offer configuration capabilities that enable VLAN segmentation, quality of service policies, port security features, and monitoring through protocols like SNMP. These features become essential in environments with multiple departments, security compliance requirements, or applications with specific performance needs. The additional management capabilities come with increased complexity and cost, but provide the control necessary for most enterprise environments where network reliability and security are priorities.
Stacking Capabilities Consideration
Stackable switches offer operational advantages in environments requiring multiple access layer devices. Stacking technology allows multiple physical switches to operate as a single logical device, simplifying management and improving resilience through cross-stack link aggregation. This approach provides simplified management through a single interface rather than configuring each switch individually, reducing administrative overhead and potential configuration errors.
Stacking becomes particularly valuable in scenarios with high inter-VLAN traffic requirements or when physical port density exceeds what single devices can provide. The technology enables flexible expansion as organizational needs grow, allowing additional switches to join existing stacks without significant reconfiguration. Not all environments require stacking capabilities, but organizations anticipating growth or managing high-density user environments should carefully consider this feature during the selection process.
Advanced Feature Considerations
Modern access layer switches increasingly incorporate features that were previously reserved for distribution or core layer devices. Layer 3 Lite functionality provides basic routing capabilities between VLANs, reducing the load on distribution layer switches for internal traffic patterns. Energy Efficient Ethernet features reduce power consumption during periods of low utilization, providing cost savings and supporting sustainability initiatives.
Advanced security features including MACsec encryption provide link-layer security for sensitive environments, protecting data as it travels between switches and endpoints. Network analytics capabilities built into modern operating systems provide visibility into application performance and user experience, helping administrators proactively address issues before users notice degradation. Programmability through APIs supports automation initiatives, allowing organizations to streamline deployment and maintenance processes while reducing human error.
Implementation and Deployment Best Practices
Successful access layer deployment begins with thorough planning that accounts for both physical and logical network design. Physical placement should consider environmental factors like temperature and humidity while ensuring adequate clearance for maintenance and cable management. Logical design should implement consistent numbering schemes, VLAN strategies, and security policies across all access layer devices to simplify management and troubleshooting.
Configuration standardization across all switches ensures consistent behavior and simplifies troubleshooting processes. Implementing baseline security configurations including disabling unused ports, enabling port security features, and requiring authentication for network access protects against unauthorized device connections. Regular firmware updates address security vulnerabilities and performance issues, though these should be tested in non-production environments before widespread deployment.
Monitoring and maintenance processes should include regular reviews of performance metrics, security logs, and capacity planning assessments. Establishing baseline performance metrics during initial deployment makes it easier to identify anomalies that could indicate developing issues. Documenting configurations, physical layouts, and logical designs ensures knowledge preservation regardless of staff changes, maintaining operational consistency over time.
The selection and implementation of access layer switches requires balancing numerous technical requirements with budgetary constraints and operational considerations. While brand reputation provides some indication of quality and support, the specific features and capabilities should align with organizational requirements rather than marketing messages. Enterprises should prioritize reliability, manageability, and scalability when making selection decisions, ensuring that chosen devices can support both current operations and future growth.
The most successful deployments result from thorough requirements gathering, careful evaluation of available options, and implementation following established best practices. By understanding the role these devices play within the broader network architecture, organizations can make informed decisions that provide reliable connectivity while supporting security and performance objectives. The right access layer switches become transparent enablers of business productivity rather than sources of frustration, forming a solid foundation upon which digital transformation initiatives can successfully build.








Leave a comment