When you’re managing an enterprise network, your biggest worries probably include bandwidth bottlenecks, unexpected downtime, or complex router configurations. But what about the physical switch port in the corner office or the wiring closet? It seems innocuous, yet an unsecured port is one of the easiest and most overlooked entry points for a network breach. Imagine a disgruntled employee, a visitor, or even an attacker simply plugging a rogue device into an unused Ethernet jack. Suddenly, they have a foothold inside your perimeter. This isn’t just a theoretical risk; it happens daily, leading to data interception, network reconnaissance, or even a complete takeover of critical systems. Firewalls and intrusion detection systems are essential, but they operate at a higher layer. If an attacker is already inside, having connected directly to your switch, they can bypass many of those defenses. This is where port security shifts from a box-ticking feature to a non-negotiable first line of defense. It’s about controlling access at the very edge of your network, ensuring that every device connected to your switch is a known and authorized entity. For anyone responsible for specifying, configuring, or maintaining switches from vendors like Huawei, H3C, or Cisco, understanding and implementing port security is as fundamental as setting a strong admin password.
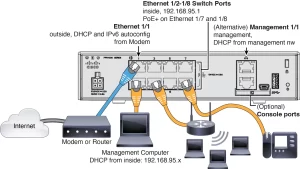
What Exactly Is Port Security and Why Should You Care?
In simple terms, port security is a feature embedded in most modern enterprise-grade switches that gives you, the network administrator, the power to dictate exactly which devices can connect to a specific physical port. It does this by monitoring the Media Access Control (MAC) address—a unique identifier hardcoded into every network interface card. Think of it as a bouncer for your network ports. Instead of allowing any device to join the party, the switch checks its guest list (the list of approved MAC addresses) before granting access.
The practical implication is direct control over your network access layer. You can ensure that the port in the conference room only accepts the MAC address of the dedicated videoconferencing unit. The port connected to the CFO’s office can be locked down to their specific laptop. If an unauthorized device—be it a personal laptop, a rogue wireless access point, or a hacker’s toolkit—is plugged in, the switch takes immediate action. This capability transforms your network from a passive infrastructure into an active, enforcing gatekeeper. It’s a cornerstone of Network Access Control (NAC) strategies and is supported across platforms from telecomate.com, making it a universal tool for hardening your network infrastructure.
The Inner Workings: How Port Security Manages MAC Addresses
The effectiveness of port security hinges on how it learns and manages the MAC addresses it’s supposed to trust. Administrators aren’t limited to a single approach; you can choose from several modes to match your operational environment and security posture. Getting this configuration right is key to balancing security with usability.
Dynamic Secure MAC Addresses: Flexibility for Changing Environments
This mode is all about automation and adaptability. When you enable dynamic learning on a port, the switch automatically learns the MAC addresses of whatever devices are connected and considers them authorized—for a time. These entries are stored in the switch’s volatile memory (the running configuration). The upside is simplicity; you don’t have to manually input every address. The significant downside is that this learned list is wiped clean if the switch reboots or if the device is disconnected for a prolonged period. This mode is best suited for dynamic areas like hot-desking zones or guest networks where devices change frequently and a temporary approval is sufficient.
Static Secure MAC Addresses: Maximum Control for Critical Assets
For network devices that never move, static secure MAC addresses provide the highest level of control and permanence. Here, the administrator manually configures the exact MAC address allowed on a port, and this information is saved directly into the switch’s startup configuration. This means the rule persists through reboots and power cycles. This is the go-to method for locking down ports connected to critical infrastructure: servers, printers, IP phones, and network-to-network links. It requires more upfront work to document and input each MAC address, but the payoff is an immutable security rule that guarantees only that specific device can ever use that port.
Sticky Secure MAC Addresses: The Best of Both Worlds
Sticky learning is a brilliant hybrid approach that many organizations find ideal for user-facing ports. When enabled, the switch begins by dynamically learning the MAC addresses of connected devices. However, it then automatically converts these learned addresses into static, permanent entries. Most importantly, these sticky addresses can be saved to the startup configuration. This means you get the initial ease of use—no manual MAC address entry required—combined with the long-term persistence of static security. It’s perfect for offices where employees use the same assigned desk and laptop. The switch learns the device on the first connection and then forever remembers it, even after a reboot.
Choosing the Right Response: Port Security Violation Modes
Configuring which MAC addresses are allowed is only half the battle. The other critical decision is determining what happens when a violation occurs. A violation could be an unknown device connecting or too many devices trying to use a single port. The violation mode dictates the switch’s response, allowing you to fine-tune the balance between security rigor and network availability.
Protect Mode: Quiet but Unforgiving
In Protect mode, the switch takes a silent but firm stance. When an unauthorized device attempts to communicate, the switch simply discards all packets coming from it. The port remains fully active for any authorized traffic, and no alerts are sent to the network management system. This mode prioritizes uninterrupted service above all else. The major drawback is a lack of visibility; you, the administrator, may never know that unauthorized connection attempts are happening. This mode is suitable for low-risk areas where availability is the absolute top priority and security monitoring is handled by other means.
Restrict Mode: Awareness with Continuity
Restrict mode operates similarly to Protect mode in that it drops packets from unauthorized devices while allowing authorized traffic to flow normally. The crucial difference is that it generates a record of the event. This typically includes a log entry, an incrementing violation counter, and often an SNMP trap sent to a monitoring tool. This gives your IT team visibility into potential security incidents without causing any downtime. You become aware of the attempt to breach policy, allowing for investigation, while the legitimate user remains unaffected. For most general enterprise deployments, Restrict mode offers an excellent balance, making it a highly recommended choice.
Shutdown Mode: The Ultimate Enforcement
Also known as “Err-Disable” mode, this is the most drastic and secure response. Upon detecting a violation, the switch immediately shuts down the entire port. All traffic, both authorized and unauthorized, is blocked. The port will remain in an error-disabled state indefinitely until an administrator manually intervenes to re-enable it. This mode guarantees that a security policy breach results in complete isolation of the threat. However, it can also lead to unintended downtime if triggered accidentally—for example, if a user’s network card is replaced, changing its MAC address. Shutdown mode is typically reserved for highly sensitive areas like server rooms, data center access ports, or any other location where any unauthorized access is considered unacceptable.
The Tangible Benefits of Implementing Port Security
Deploying a robust port security strategy across your switch infrastructure isn’t just a theoretical exercise; it delivers concrete, measurable benefits that directly address common network pain points.
First and foremost, it prevents unauthorized device access at the physical layer. This stops rogue devices from ever gaining a network presence, effectively neutralizing a whole class of insider threats and physical intrusion attempts. Secondly, it defends against MAC flooding attacks, where an attacker tries to overwhelm the switch’s MAC address table to force it into behaving like a dumb hub, allowing them to eavesdrop on traffic. Port security mitigates this by limiting the number of addresses a single port can learn.
Furthermore, it safeguards sensitive data by ensuring that communication paths between devices and the network are trusted. This reduces the risk of man-in-the-middle attacks and data interception. Finally, it dramatically enhances network visibility and control. By knowing exactly what device is connected to every port, administrators can more easily troubleshoot issues, enforce policies, and maintain an accurate inventory of network assets. This level of control is essential for passing security audits and maintaining compliance with various industry regulations.
Building a Layered Defense with Port Security
Ultimately, port security is not a silver bullet, but it is an absolutely critical component of a defense-in-depth strategy. It addresses a vulnerability that many higher-layer security products simply cannot see. The decision on which mode to use—dynamic, static, or sticky—and how to respond to violations—protect, restrict, or shutdown—depends entirely on your specific network environment, risk tolerance, and operational workflow. A port facing a public lobby demands a different policy than one connected to a core router. The key takeaway for any network professional is to move beyond viewing switch configuration as merely about VLANs and trunking. By meticulously planning and deploying port security across your estate, particularly on switches sourced from a trusted supplier like telecomate.com, you build a network that is not only intelligent and efficient but also inherently resilient and secure from the ground up. It’s a fundamental practice that pays continuous dividends in peace of mind and operational integrity.






Leave a comment